One37 Identity Platform
One37 delivers a suite of Digital Trust building blocks to power complete Decentralized Digital Identity solutions, providing the highest level of security, and privacy for businesses and consumers.
We do this by designing our systems according to the design principles and methodology of Self-Sovereign Identity or SSI.
Self-Sovereign Identity:
The Path To Self Sovereign Identity - Christopher Allen Self-sovereign identity is the next step beyond user-centric identity and that means it begins at the same place: the user must be central to the administration of identity. That requires not just the interoperability of a user’s identity across multiple locations, with the user’s consent, but also true user control of that digital identity, creating user autonomy
- SSI solutions attempt to implement a decentralized approach to digital identity, which seeks to eliminate the need for centralized identity authorities and give individuals/businesses more control over their own digital identities.
- SSI enables individuals to create and manage their own unique digital identities, which can be verified and trusted by others without the need for a central authority.
- SSI can be used in a wide range of applications, including online identity verification, secure access control, and digital payments.
- SSI will ensure convenience, privacy for business and users while keeping data security at its best state with tools like Zero Knowledge proofs or data minimization.
- One37's SSI implementation is built on an evolving set of technologies and standards, peer-to-peer networking, and cryptographic protocols.
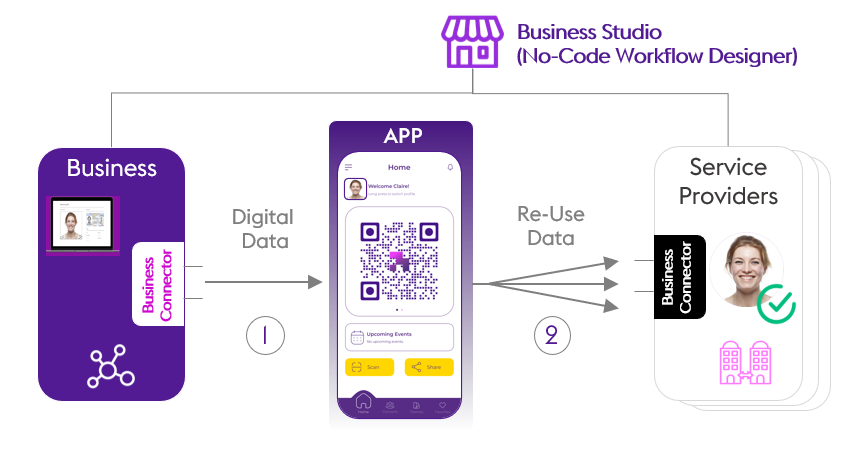
Issuer (Business)
Issuers are the source of data in an ecosystem. They transform their raw data about a subject into Verifiable Credentials that are usable more broadly via the user’s wallet. Common examples of issuers include universities issuing diplomas, insurance companies issuing insurance cards, and libraries issuing library cards—but with digitally-native identity, so many more possibilities open up.
Google’s “State of API Economy 2021” reportEvery company in the world already has valuable data and functionality housed within its systems. Capitalizing on this value, however, means liberating it from silos and making it interoperable and reusable in different contexts
The value for issuers often stems from extending their existing business into a new, digital format, which can either reduce costs or increase revenue.
Issuers deploy and integrate the One37 ID Business Connector to enable existing business processes to Issue credentials to Holders.
Holder (APP)
Holder is the umbrella term for the person or organization who controls the identity credential data in question. Whenever possible, the identity solution design should put the holder in control of their own identity. The holder should always be able to give consent before their data is shared.
Usually, the “subject” of the identity and the holder are the same. When Alice controls an identity wallet filled with Alice’s credentials, the holder and subject are the same. However, if Alice is a 2-year-old child, it’s likely that Alice’s father, Bob, will control her wallet. In that case, Bob is the holder and Alice is the subject. The holder and subject can also differ for business wallets, refugee/homeless/incarcerated person wallets, or for inanimate objects.
Individuals as Holders manage their identity credentials in the One37 Identity Wallet application installed on their mobile phone.
Verifier (Service Providers)
Verifiers, sometimes also known as Relying Parties, are the organizations that need to verify the identity of a person or organization. They’re the ones who need to know that Alice is over 21, that Bob is a licensed driver, or that Charlie is a citizen of the United States. Verifiers are the ones who need to know that the credential they’re seeing is valid and hasn’t been tampered with.
Verifiers are the big winners of the move toward digital identity. They’re able to verify people with less friction and more trust, all with less expense than current systems.
Verifiers also deploy a One37 ID Business Connector to enable existing business processes to request verifiable data from Holders.
Credentials
"Verifiable Credentials," or "VCs" are standardized, cryptographically-signed documents that attest information about an entity. They provide an interoperable way to attest and authenticate any kind of data in an IDtech application.
infoA verifiable credential is a set of tamper-evident claims and metadata that cryptographically proves who issued it.
Verifiable credentials are unique from other kinds of digital documents because they enable you to verify the following things:
- The original issuing entity (the source of the data)
- It was issued to the entity presenting it (the subject of the data)
- It hasn't been tampered with (the veracity of the data)
- Whether the issuer revoked the credential as of a particular point in time (the status of the data)
The Verification Process
The Verification Process is the overall mechanism for requesting (Proof Request), consenting, and authenticating the returned data (Proof Response) from the verifiable credentials in an identity wallet.
Components of a Verification Flow
Proof Request / Presentation Request
The data structure sent by a Verifier to a Holder that describes the specific attributes of Credential/s required by the Verifier to be returned in a Proof. Proof Requests are sent and received using a variety of mechanisms.
Proof / Presentation (aka Proof Response)
The response from a Proof Request is a data collection that allows for the Cryptographic verification of the included Credential Attributes. A digital signature is a simple form of Proof.
If a Predicate attribute is specified in the Proof Request, it is returned as a Zero Knowledge Proof.
Zero-knowledge proofs
A zero-knowledge proof (ZKP) allows a user to prove some information is true without revealing the information itself. The classic example is proving you’re over 18 without revealing your birthdate.
The most important application of zero-knowledge proofs today is the ability to perform selective disclosure on the contents of a verifiable credential. This is important for the obvious privacy reasons related to data minimization, but it’s also important for the less-obvious privacy reasons of obfuscating correlate-able identifiers from verifiable presentations. Current ZKP capabilities only allow mathematical computation on numerical attribute values, such as "is GPA > 3.0"